From Sub domain Takeover to Open-Redirect
Hey guys,
I am Anil Tom. Since I haven’t written a blog for a while, I just thought of writing one. Today, I am going to share one of my findings in Bugcrowd Private Bug Bounty Program.

After a long break, I logged in to my Bugcrowd Account and while checking the programs I noticed that there were some pending private program invitations. On further checking, one program grabbed my attention. So I selected that program and checked its scope. There were around SIX Domains in scope for that program, so I started opening each website.
While checking, I found that one website was greeted by this Godaddy web page
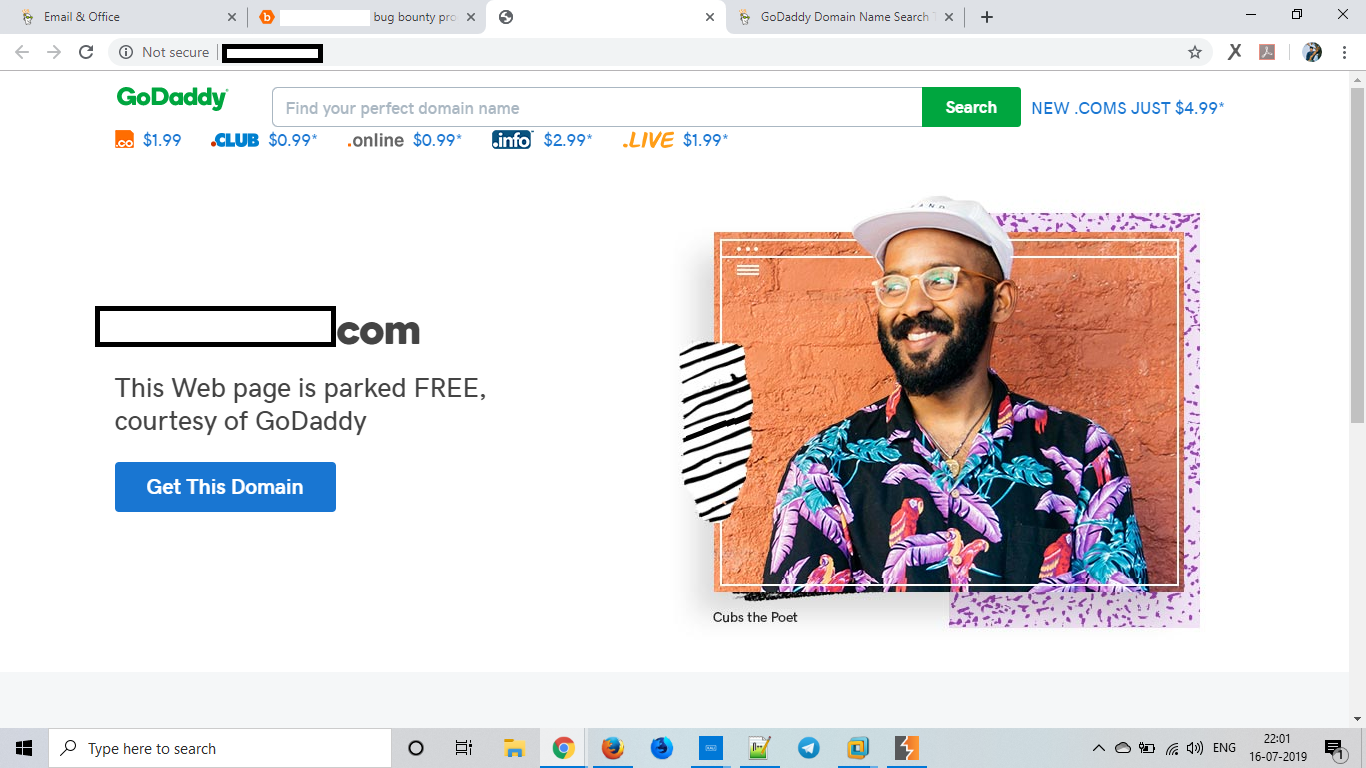
When I saw this page I was like “heyyyyy!!! Sub Domain Takeover.”

But when I checked it further and saw this
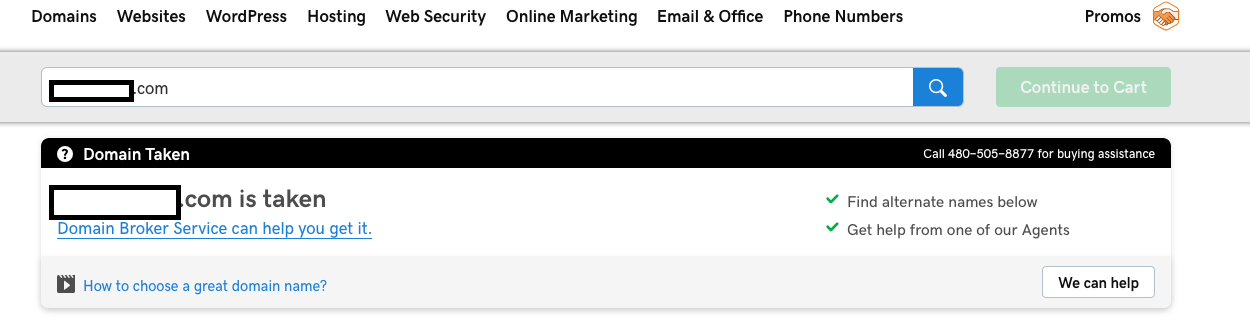
It was not expired :( the sub domain takeover was not possible

And as I was closing the tab, suddenly my mind said, why not try recon on this website. So I checked Domain Name Registration Data Lookup using https://lookup.icann.org/lookup and discovered that it was owned by the company itself. So I ran dirsearch against the domain but I could not find anything.
Then I checked whether this web site was Vulnerable for Open-Redirect ?
What is Open-Redirect Vulnerability?
Open-Redirect is basically is not a high impact vulnerability , A web application accepts a user-controlled input that specifies a link to an external site, and uses that link in a Redirect. This simplifies phishing attacks.
Open redirection is listed in the OWASP Top 10 for 2013 and 2010 (10th position in both lists) since it is still an active threat in modern web applications. Open redirection occurs when a vulnerable web page is redirected to an untrusted and malicious page that may compromise the user. Open redirection attacks usually come with a phishing attack because the modified vulnerable link is identical to the original site, which increases the likelihood of success for the phishing attack.
Open redirection is listed in the OWASP Top 10 for 2013 and 2010 (10th position in both lists) since it is still an active threat in modern web applications. Open redirection occurs when a vulnerable web page is redirected to an untrusted and malicious page that may compromise the user. Open redirection attacks usually come with a phishing attack because the modified vulnerable link is identical to the original site, which increases the likelihood of success for the phishing attack.
The target let’s just say it was named redact.com. I changed the URL to https://redact.com//google.co.in/ and executed it and as expected I got a redirect to https://google.c

Then I made a PoC video and reported it to the Team
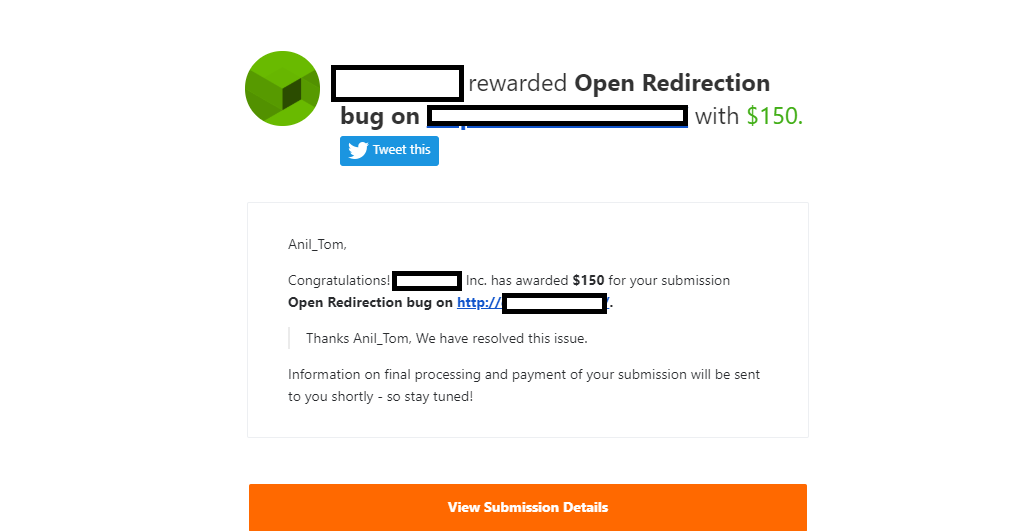

No comments
Please do not enter any spam link in comment box.