How i bought my way to subdomain takeover on Tokopedia
After reading their rules, I noticed that the targets is mainly set to wildcard domains (*.tokopedia.com and *.tokopedia.net). So i began to enumerate the subdomain using a couple of open source tools like sublist3r, knockpy, massdns, etc.
I found some interesting subdomain (more on this on the next write-ups). But the one that catches my eyes is REDACTED.tokopedia.com, because when i access the subdomain, i was getting an ERR_NAME_NOT_RESOLVED error page from my browser.
Using dig command in my terminal, turns out that the CNAME configuration is pointing to another Top Level Domain (REDACTED.com). So REDACTED.tokopedia.com is actually an alias for another different domain which is REDACTED.com.
Surprisingly, when i checked the whois record, the domain is actually expired. So i head straight up to namecheap.com to check if it’s available to buy, and well, it is.
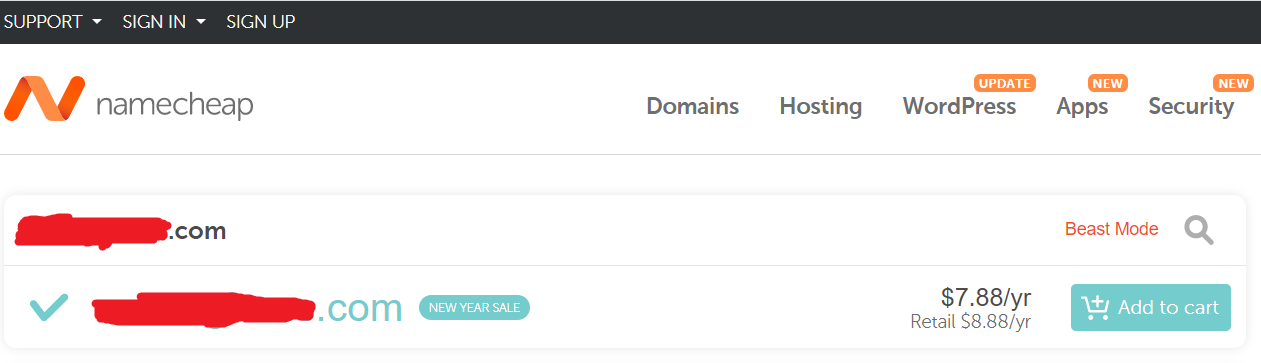
Here comes the dilemma, I was really broke at that time (no, seriously), i can’t even afford a domain for 8 bucks, PLUS, i’m still not sure whether this subdomain is actually takeoverable or not. I even consider to report this vulnerability without buying the domain, but i don’t think that’s a good idea.
So, decided to take the risk, borrowing 8 bucks from my friend (yes, no kidding), then bought the domain.
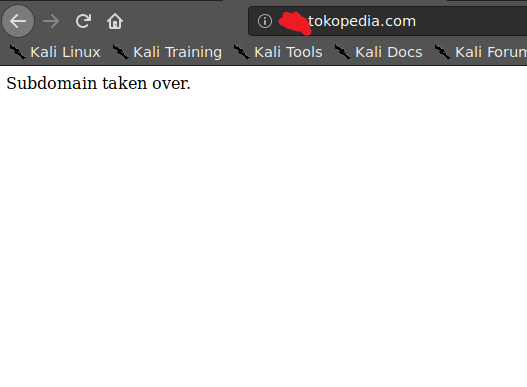
After pointing it to a free hosting service, i try to open the subdomain again, and well, i successfully taken over the subdomain because it’s now pointing to my own server.
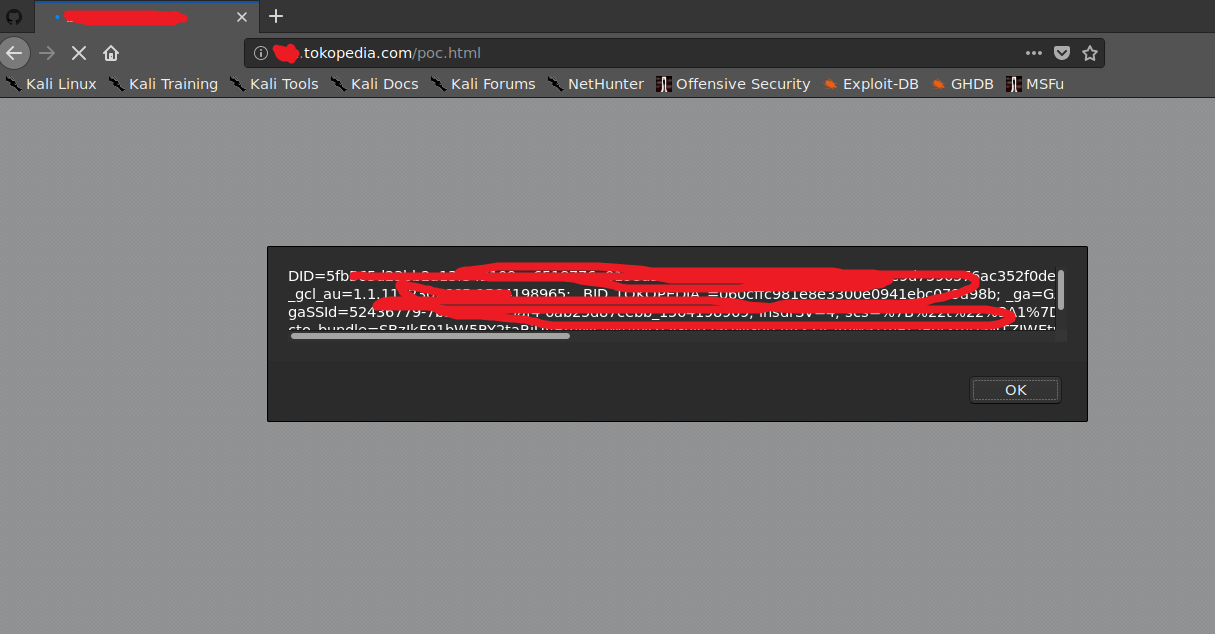
I decided to make some PoC for XSS, but stumble upon a problem because the cookies is set with secure flag, so the site needs to be hosted in https. After i set a free SSL certificate for REDACTED.com, another problem arise, the browser throws a privacy warning, because the site is accessed from REDACTED.tokopedia.com, while the certificate is signed for REDACTED.com.
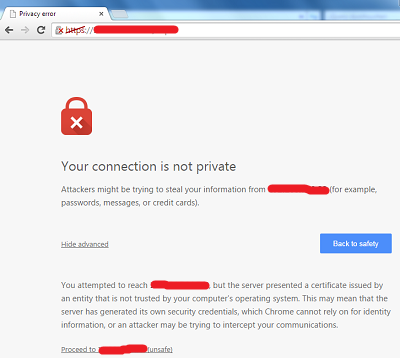
They won’t allow me to make a *.tokopedia.com SSL certificate, so i decided to report it right away. We could still steal cookies if the user decided to click proceed to… button anyway, so yeah.
NOTE: If you found a subdomain takeover, i think it’s not wise to show something unnecessary on the front page, the company won’t like it because user could saw it, and it’s bad for their reputations. This report is from my earlier days as a Bug Bounty Hunter, so showing “Subdomain taken over” on front page might not be the best idea. Instead, we could write our PoC on hidden html tag, and maybe showing “Under Maintenance” on the front page. And don’t forget to randomize the file name we hosted on that subdomain so it won’t be accidentally found by users.
Well, the Security Team verified my report, and it’s a valid security bug with High Severity, and they decided to reward me with $$$.
Spending $8 for $$$ rewards? I see this as an absolute win.


No comments
Please do not enter any spam link in comment box.