XSS on Sony subdomain

Hi guys. This is my first bug bounty writeup. I started to bug bounty on july 22, 2019. I want to share with community all the vulnerabilities I have found.
I choose for large scope programs when looking for bug bounty programs and for improve myself I don’t care about bounty now. So I chose SONY.
I started with subdomain enumaration. Firstly, I used crt.sh and I use the following to find potential sub-domains.
%my%.sony.net
%jira%.sony.net
%jenkins%.sony.net
%test%.sony.net
%staging%.sony.net
%corp%.sony.net
%api%.sony.net
%ws%.sony.net
%.%.%.sony.net
Sometimes just random letters..
%p%.sony.net
%i%.sony.net
%ff%.sony.net
%co%.sony.net
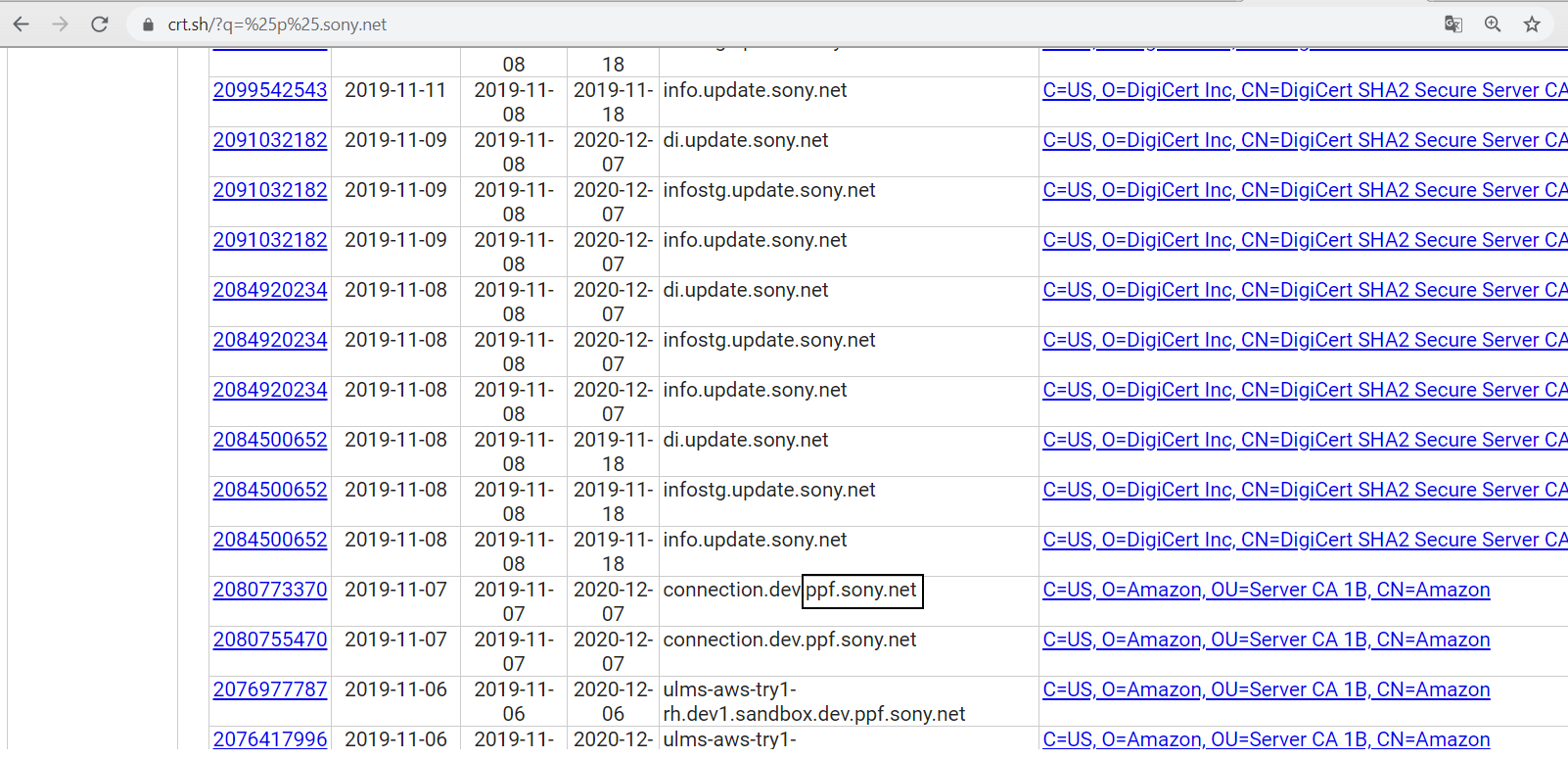
I found this one (ppf.sony.net). Then, I used assetfinder and httprobe by tomnomnom for subdomain enumeration and I found a deep sub-domain. Here is our target sub-domain. authtry.dev2.sandbox.dev.ppf.sony.net
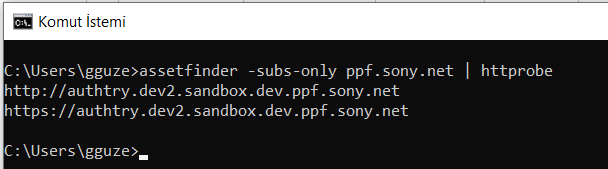
assetfinder -subs-only ppf.sony.net | httprobe
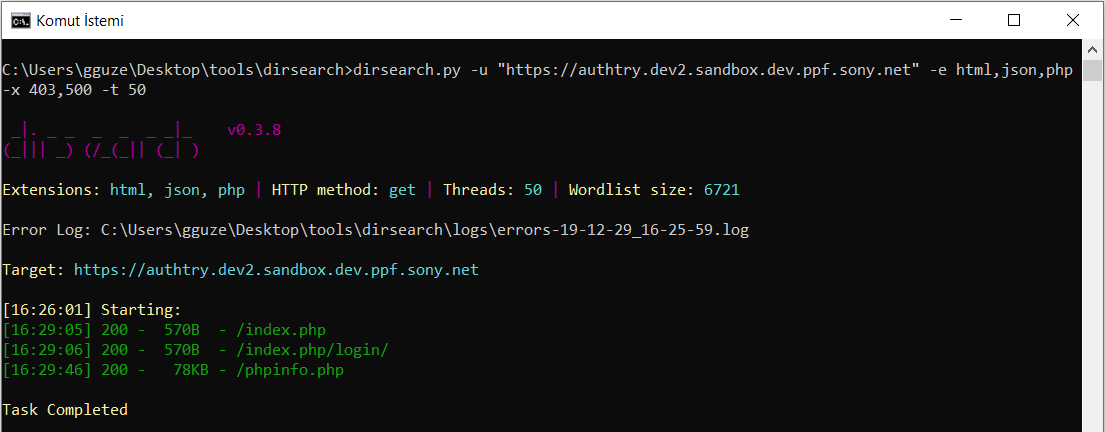
Then, I used dirsearch for secret directories. The default page appeared.
dirsearch.py -u “authtry.dev2.sandbox.dev.ppf.sony.net” -e html,json,php -x 403,500 -t 50
When I visit to index.php I got this page.
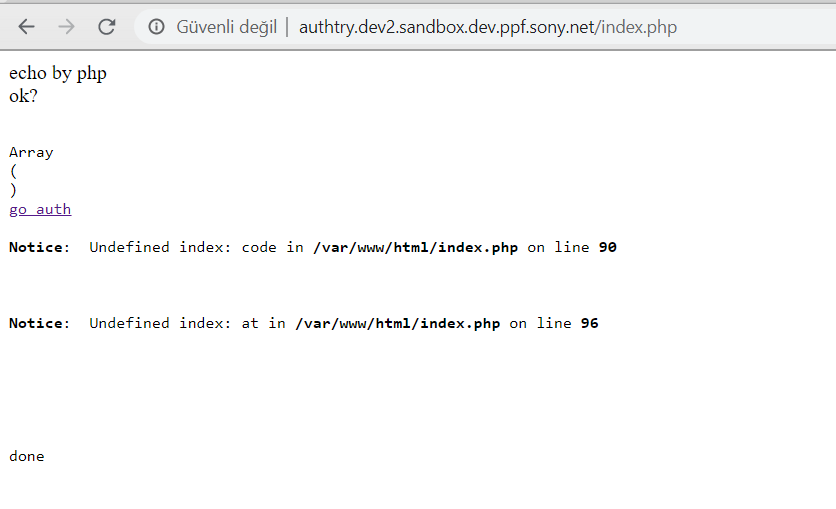
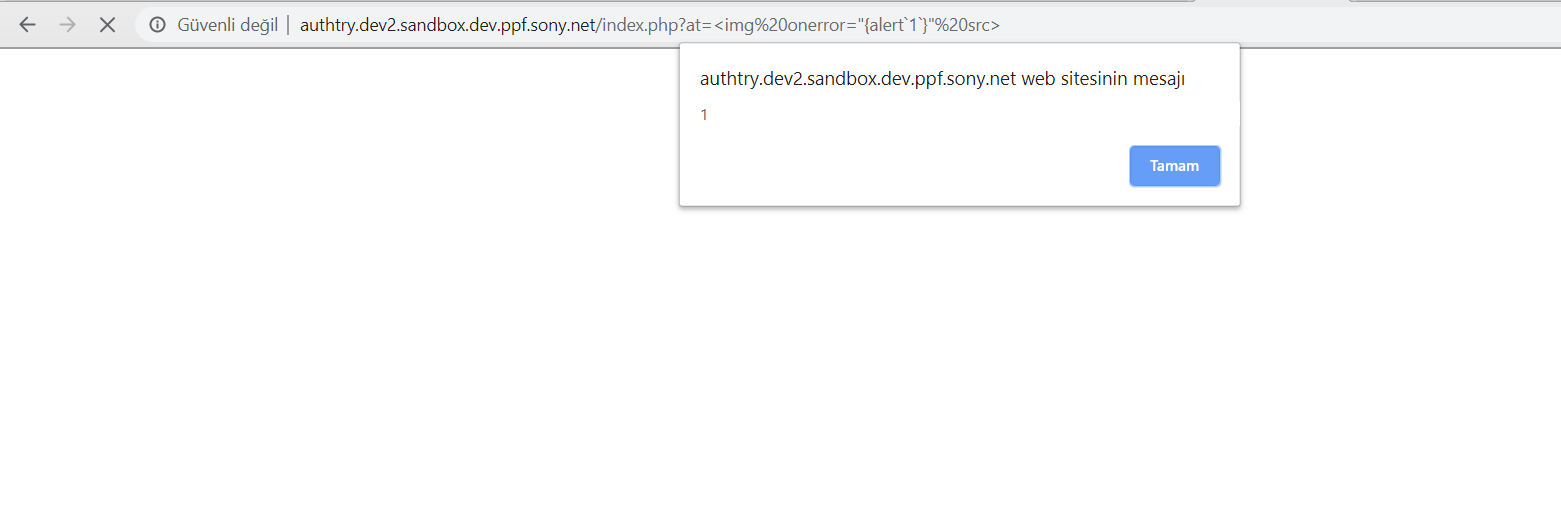
As you can see we have 2 parameters and if you have parameters on the empty page, firstly try to get XSS. I tried get xss on the page and I got !!
Also my favorite payload : <img onerror=”{alert`1`}” src>
Thank you !!!

No comments
Please do not enter any spam link in comment box.